"Imagine three or four different work groups. One of them will be stronger than the others. To increase in importance, the weak have only two options: ally themselves with the strong or cooperate with one another. Mathematics tells us that cooperation is usually the best strategy for the weak and, interestingly, that it is also the most beneficial for all. In addition, any of the weaker ones alone can force this situation, a power that the strong lack." Jacobo Aguirre, a scientist at the Centro Nacional de Biotecnología of the CSIC (CNB-CSIC), thus explains his most recent study published in the journal Nature Communications with Jaime Iranzo of the NIH (USA) and Javier M. Buldú of the Universidad Rey Juan Carlos and Center for Biomedical Technology (UPM).
The study focusses on understanding the relationships between communities in the form of networks that compete to achieve importance (what researchers term a network of networks). In their study, the authors combine game theory (known for the studies that brought the Nobel prize to John F. Nash) and the science of complex networks.
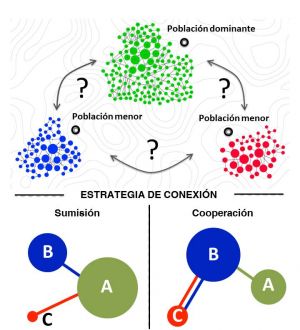
In this game, there are only two stable solutions: cooperation or submission. The first is beneficial for weak competitors and the second is positive for the strongest. The results of the study clearly show that the first option is also the best for the whole.
But it is more surprising that each of the weaker communities can cause a transition from a system of submission to the powerful to a cooperative system. "Any weak competitor has the power to induce an overall strategy change no matter what the actions of the strong competitor, who is unable to change the situation. This is the great power of the defenseless. They have the fate of the whole in their hands", explains Javier M. Buldú.
According to the authors, this line of work arose when they studied evolutionary processes in RNA sequences, but the theory is applicable to a multitude of games and real-life situations. For this study, the scientists analyzed real examples of economics, biology and social relationships.
Microcredit in India
In a first example, the paper analyzes a network of interactions among three southern Indian villages in the context of a microcredit programme. The study shows how the authorities in one of the smaller villages could promote connections with neighboring communities to minimize the financial risks associated with insect pests or weather phenomena that could affect the plantations on which the village depended.
The dilemma arises when deciding with whom to form alliances. They can choose to associate with the most important city in the region, a model in which the main beneficiary would be the latter. The alternative option, that is, association between weak populations, would allow them to surpass the strong city. "The result of our work is clear: this is the best option from the global point of view", explain the authors.
Ebola research
Several research groups around the world are working to unravel the mysteries of the Ebola virus. This is the second example the authors highlight in their work.
The study analyses the potential collaborations of virologists at Oxford University with other European centres. In this scenario, the university would have to decide what strategy is best for them to back, i.e., with whom to associate. "We believe that the theory we present in our study can help research centres to take the best possible decision when seeking collaborations," they indicate.
Connecting fragmented habitats: conservation of the brown bear
For decades, efforts to conserve the brown bear in the Pyrenees have been coordinated by Spain, France and Andorra. Each country has its own reserve areas; ecological corridors are established between them, through which the bears can move from one reserve to another. This is a good example of how, to benefit a protected species, three or more administrations must often coordinate to establish routes between their protected areas. The new study sheds light on the most efficient way of establishing such corridors, optimizing movement and recovery of the species.
Ultimately, the authors conclude, "the broad applicability of this model makes the 'power of the weak' a concept to be considered from now on in the modeling of technological, biological and social systems."
- Jaime Iranzo, Javier M. Buldú and Jacobo Aguirre. Competition among networks highlights the power of the weak. (2016) Nature Communications DOI: 10.1038/ncomms13272